Mining Vulnerable Git Repositories
The TAVM framework provides a module which can be used to extract vulnerable Git repositories from CTI data. The extracted repositories can then be linked to the corresponding STIX documents for further analysis.
How it works
A transformer adapter is used to extract Git repository URL's from the raw CTI data. Other transformers, which convert the raw data into STIX, add a custom TAVM ID property to the STIX documents which allows a link between the STIX document and the Git repository.
For each Git repository, the following data is stored:
- Repository URL: the URL of the Git repository
- Repository Type: the type of the Git repository, for example GitHub, GitLab, etc.
- Timestamps: the timestamps of when the repository was first found and when it was last updated
- Related CTI records: a list of related vulnerabilities (TAVM Unique IDs) and a timestamp of when the vulnerability was first related to the repository
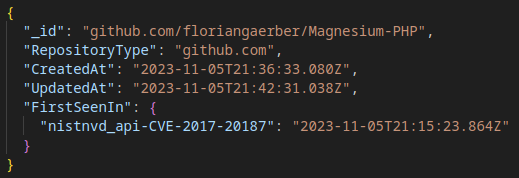
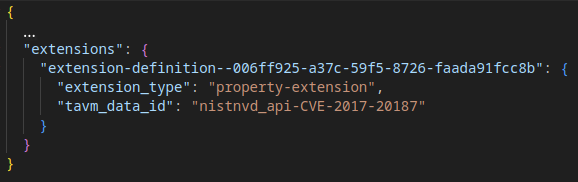
The ID which is listed in the Related CTI records (see FirstSeenIn property) can be used to link related STIX documents (see tavm_data_id extension property) to the Git repository. The STIX extension definition which contains the TAVM ID always has the identifier extension-definition--006ff925-a37c-59f5-8726-faada91fcc8b.