TAVM - A Threat And Vulnerability Mining framework
The threat and vulnerability mining framework implements a modular approach to collect cyber threat intelligence data from various sources and convert the gathered data to a machine readable STIX 2.1 format.
Get started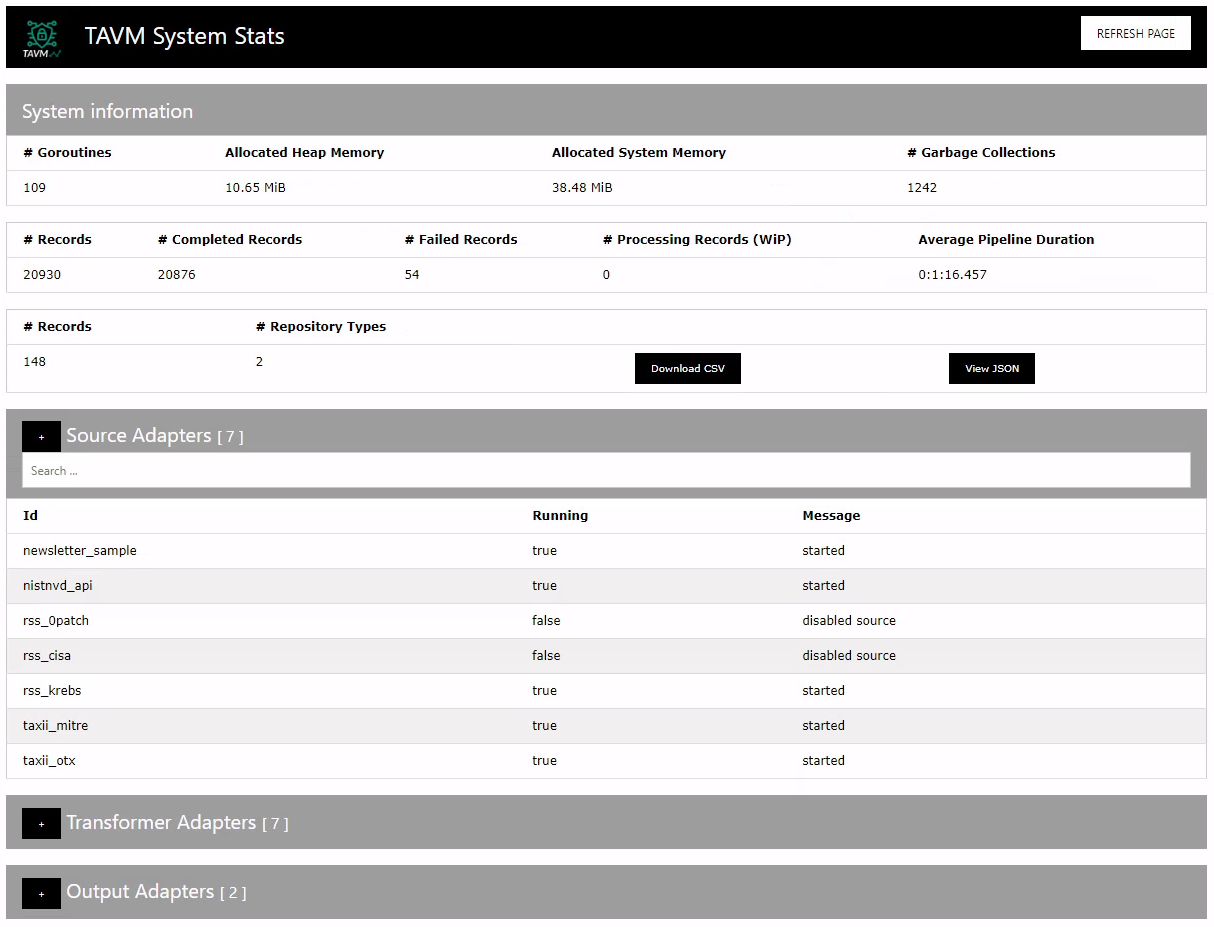
Concept
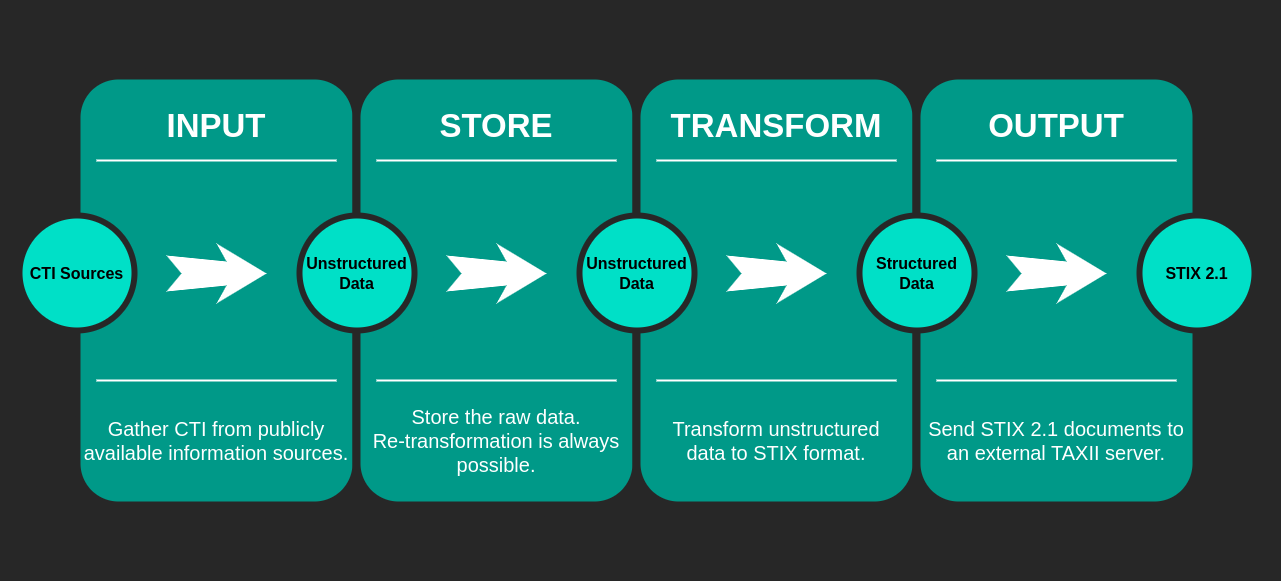
TAVM uses a modular approach to collect cyber threat intelligence data from various sources. The main processing pipeline consists of three stages: Input, Transformation and Output. Each stage can be extended with custom adapters to support additional data sources or to provide custom transformations. Predefined adapters are available for the most common data sources.
Explore features
Input Sources
Specify the input sources for the framework. You can also add your own input adapters.
Data Transformation
Configure the transformation stage. You can provide unique transformations for each input source.
Data Export
The gathered data can be exported to other systems via TAXII. Repository mining data can be exported via REST API.
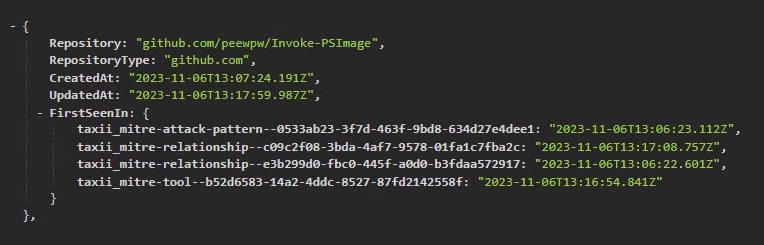
Git Repository Mining
With TAVM, it is also possible to mine vulnerable Git repositories from public sources like Github or Gitlab. The framework can extract repository information from publicly available cyber threat intelligence sources and create a comprehensive list of vulnerable repositories.
The list of vulnerable repositories can be downloaded as CSV file or can be directly exported as JSON for further analysis.